The best way to retain your hard earned competitive advantage is to prevent security threats and control repository access. Security, configuration, and compliance are all necessary to lead your market.
Hosted on Your Servers
By hosting your code in a secure behind-the-firewall environment within your business, you control all aspects of source code protection and reduce the risk of security breakthrough and IP theft. This includes not only who has administrative access to accounts and network access to the service, but also physical access to the hardware the service is running on.

Active Breakthrough Prevention
Validate users, commits messages and clients using custom extensions to prevent unwanted data in your repositories. Repository rule notifications can alert system administrators of suspicious activities, users can also be automatically locked out if they breach configured parameters. All in order to secure your precious intellectual property.
Compliance and Auditing
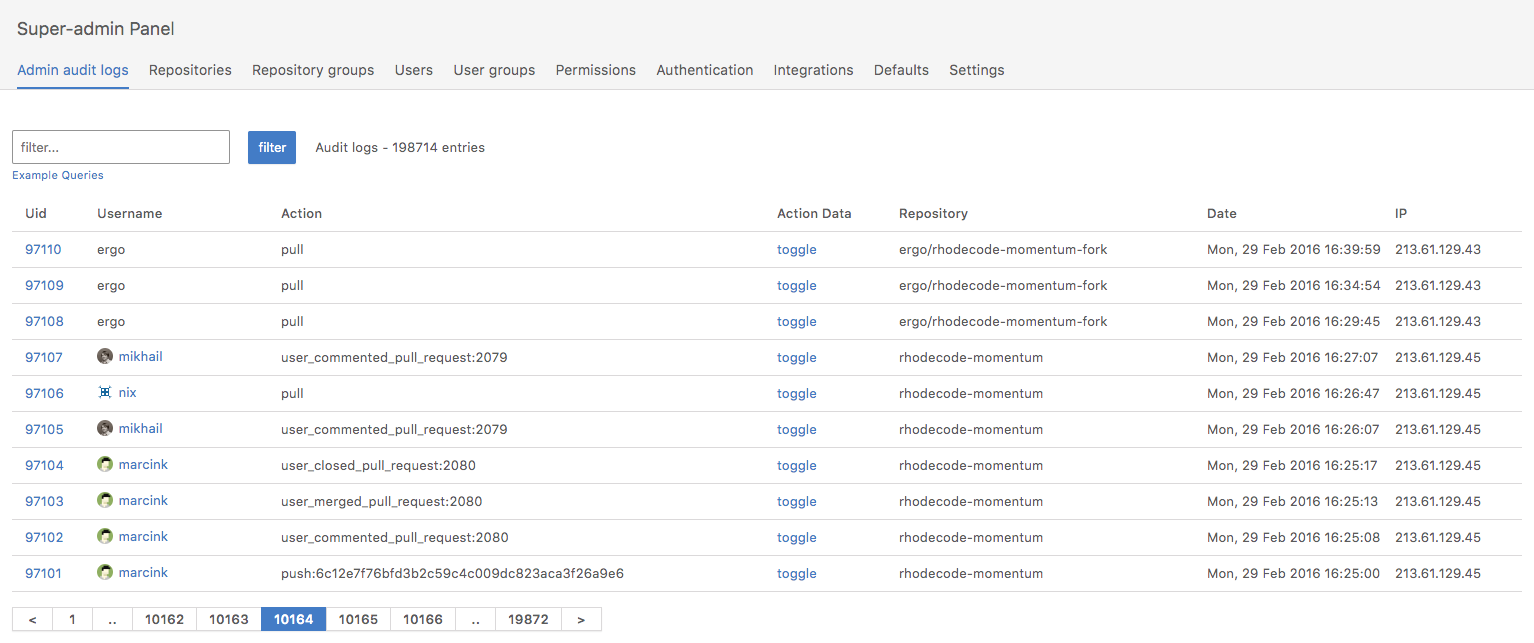
RhodeCode provides the data aggregation, analysis tools, and reporting needed for your enterprise compliance requirements. By logging every user interaction together with IP, action, and data changes, RhodeCode makes it possible to locate and visualize information regarding access, permission changes, file changes, and downloads of files. You can pinpoint activities, offering clarity and confirmation when you need it. All under single audit-log page with option to export the audit data to 3rd party systems. In Addition our code-review system is also compliant with most of certifications currently present. Approved for usage in Banking, insurance and other strong-security oriented organizations.
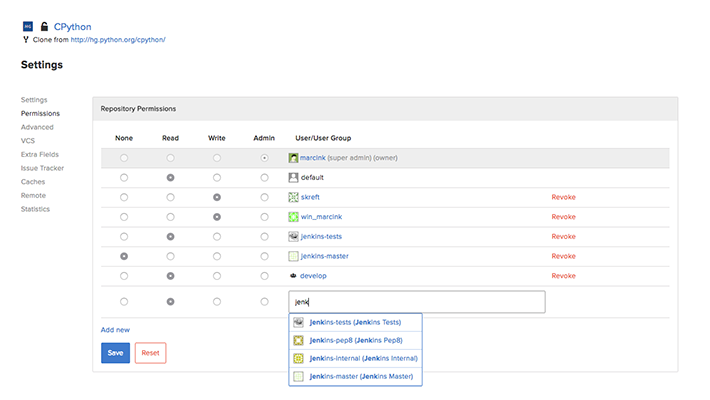
Repository Permissions
Define and manage default permissions for users, user groups, repositories, and repository groups from the permissions panel. This enables you to always stay on top of who has access to highly sensitive information. Default permissions safely corral new users based on the default user rights set by the user group, until tailored access is needed.
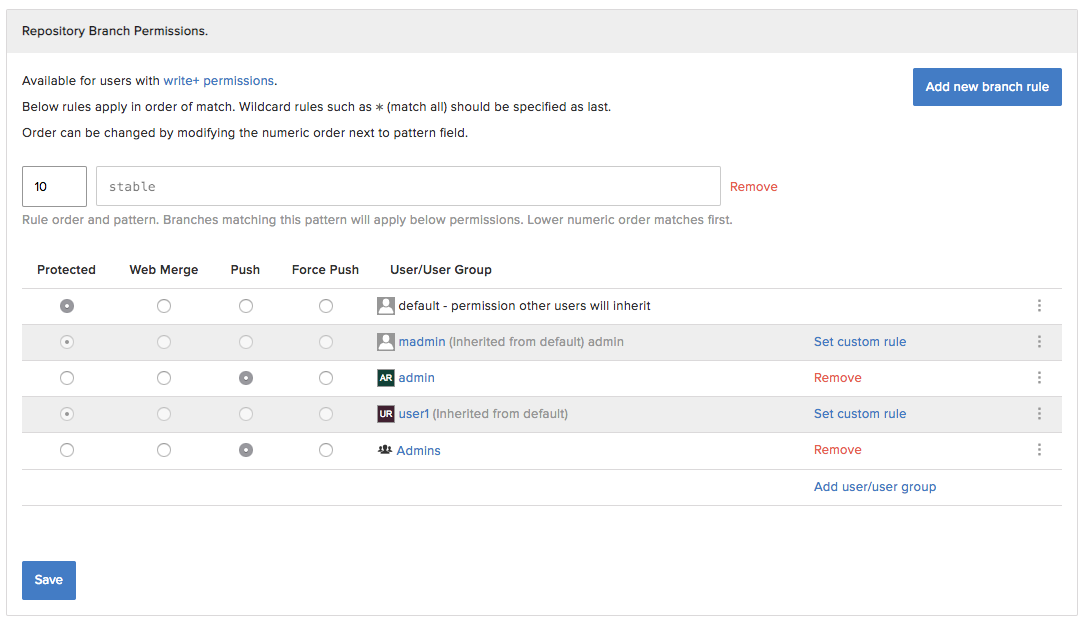
Repository Branch Permissions
With one of the most advanced branch permissions system get in control of what branches are allowed to be modified. Forbid force push, allow only web-based merges, or completely protect branch from modification. Ensure that your master/stable branches are not modified by accident in any case. All based on advanced pattern rules, and driven by our enhanced permissions controls with inheritance and audit-logs
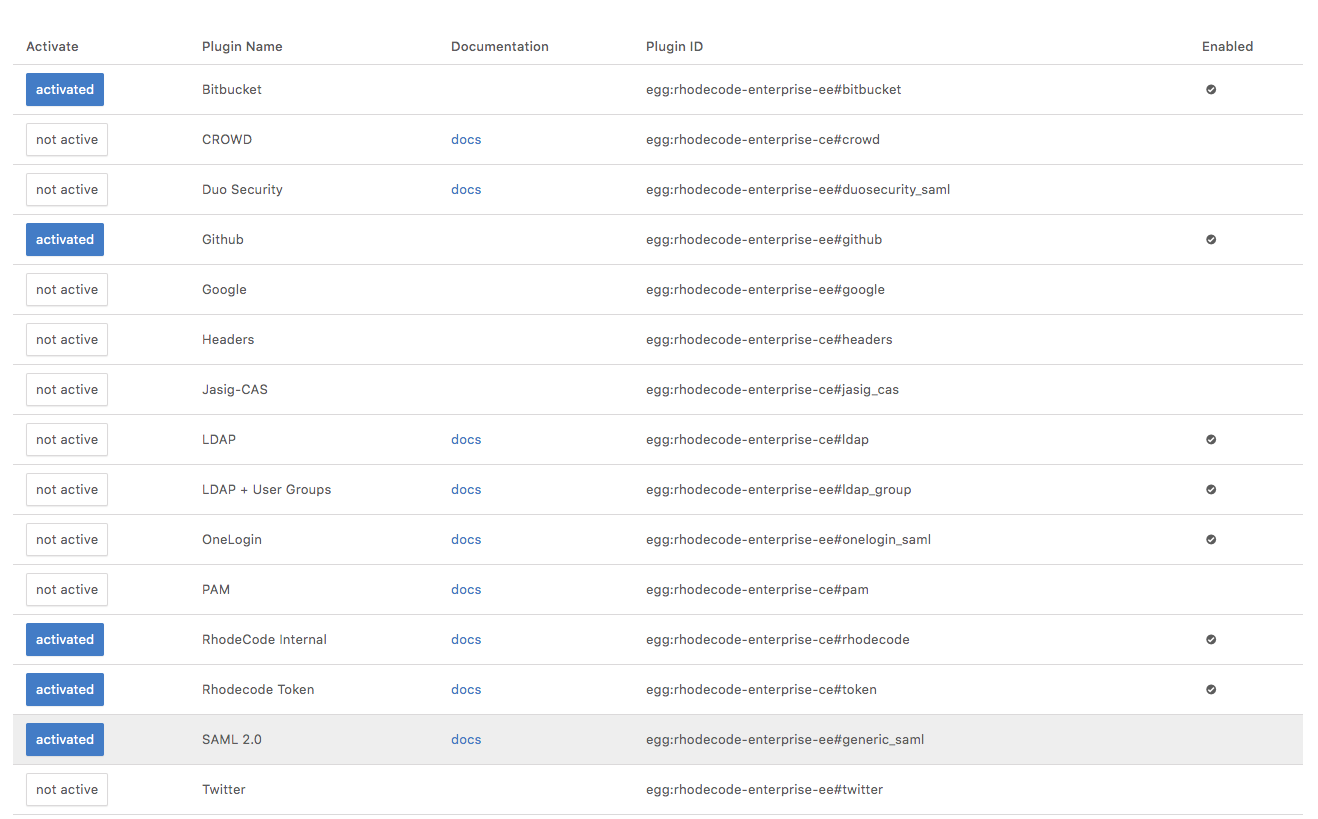
Pluggable Authentication
RhodeCode supports major authentication methods including SAML, OAuth, LDAP, LDAP with User Groups (RFC2307 and RFC2307Bis), and Active Directory. In addition there are 3rd party authentication methods allowing authentication via Google, Twitter, Github and BitBucket. RhodeCode makes it easy to mirror your company's existing organizational structure making that aspect of configuration simple.
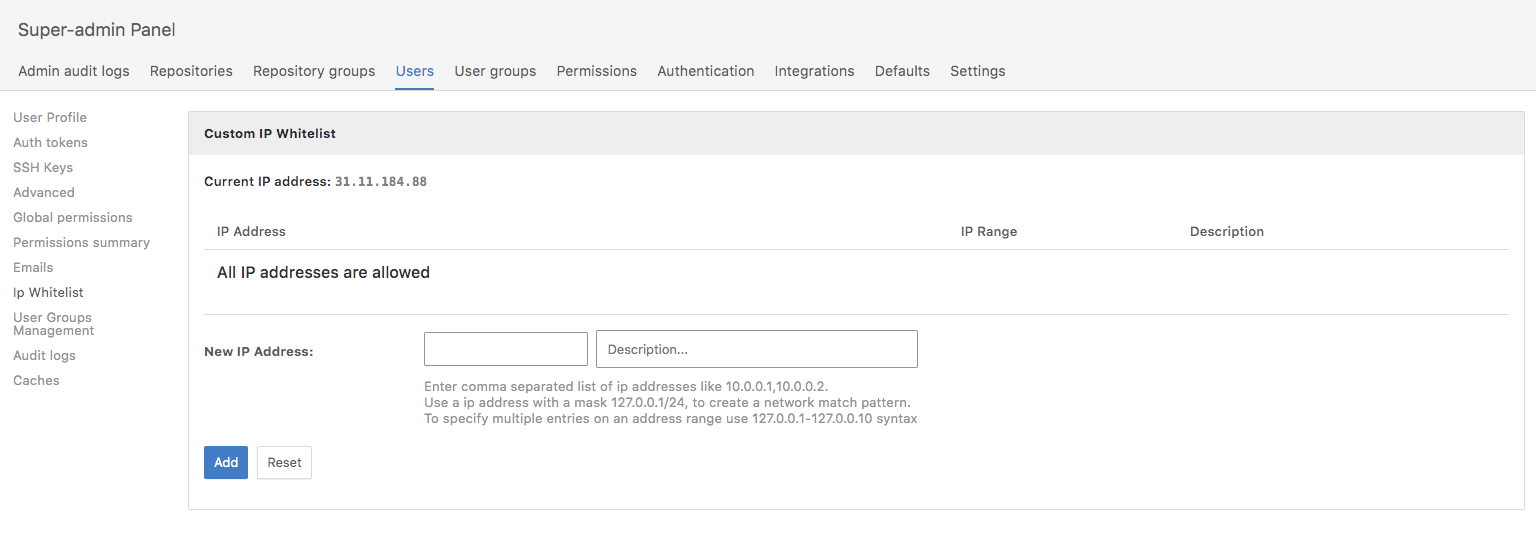
IP Restrictions
RhodeCode Offers an unique feature to allow user accounts be limited to certain IP or IP Ranges. Restrict your vendor accounts, or CI server to set of IP to ensure safest possible access to RhodeCode System.
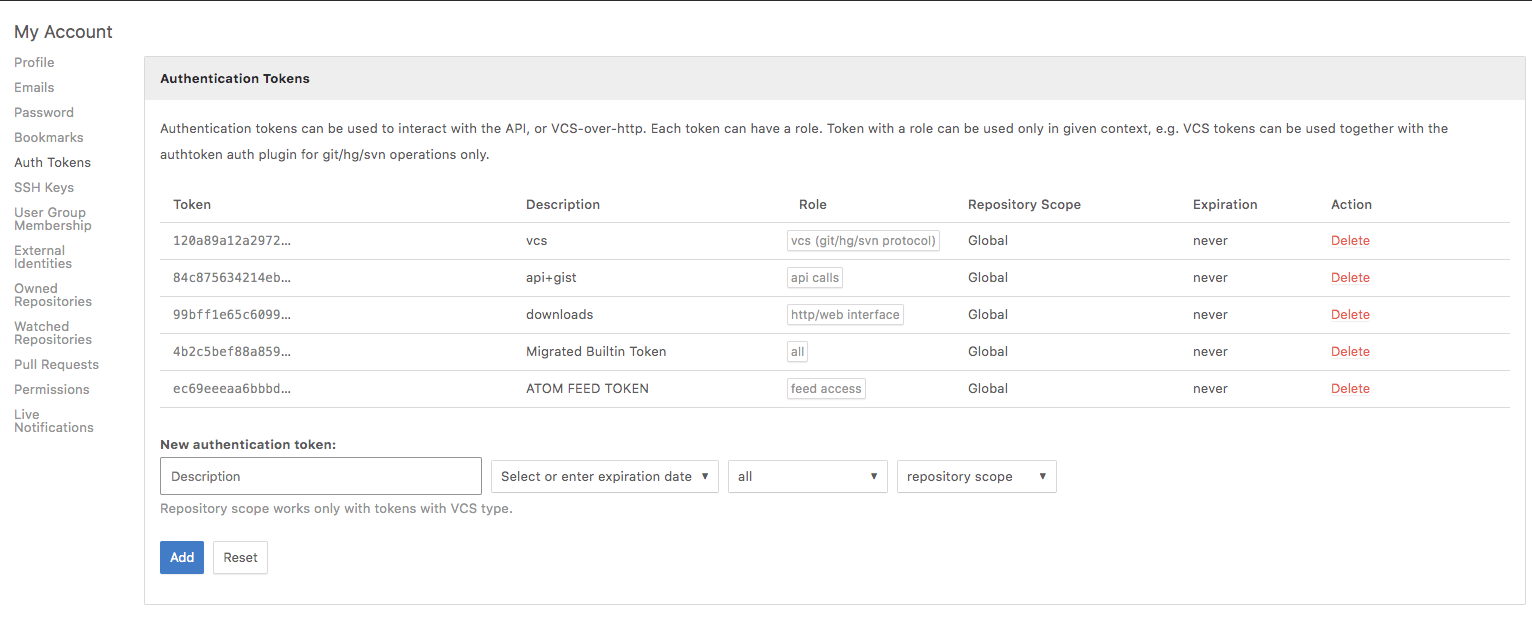
Authentication Tokens
Authentication tokens gives high flexibility on authentication and access control in RhodeCode. Create app specific tokens with set expiration time and repository scope. Share them to vendors, or use in external systems that needs to be restricted with VCS or API access without exposing any passwords. Authentication tokens are also used for API, RSS/ATOM Access, or Artifacts.